Cybercrime , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks
Mass Distribution of Self-Destructing Malware in Ukraine
Attackers Use Phishing Mails with 'Chemical Attack' Theme to Lure Victims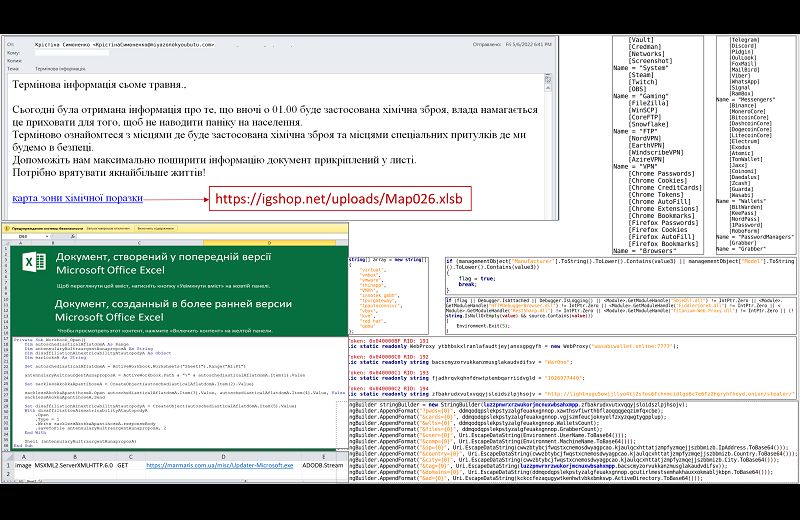
The Ukrainian Computer Emergency Response Team, which operates under the State Service of Special Communication and Information Protection of Ukraine, says an unknown attacker has been conducting a "massive" Jester Stealer malware distribution campaign to steal personal data.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
The attacker has been distributing the malware via phishing emails with a "chemical attack" theme, the CERT-UA statement says. Opening the XLS-document attached in the phishing email enables macros that download and execute an EXE file, which in turn loads the Jester Stealer malware onto the victim's system.
The malicious file is uploaded from already compromised web resources. This implies that the threat actors are using resources that are already compromised instead of their own for malware distribution to avoid leaving a trail that could lead back to them.
The malware, CERT-UA's experts say, is being used to steal authentication and other forms of data from internet browsers, MAIL/FTP/VPN-clients, cryptocurrency wallets, password managers, messengers and game programs.
One striking difference between the Jester Stealer malware and other malware, according to cybersecurity experts, is that Jester Stealer transfers all the stolen data to a malefactor via Telegram, while other malware traditionally uses a command-and-control server. "The hackers get the stolen data via Telegram using statically configured proxy addresses (e.g. within TOR)," CERT-UA experts say.
Further Decoding the Stealer
In February 2022, Cyble, a global threat intelligence software-as-a-service provider, categorized the Jester Stealer malware as .net-based, and shared a modus operandi similar to that provided by CERT-UA.
According to Cyble's technical analysis, the malware is linked to a GitHub profile. Researchers at the firm say that "in the later part of an infection, the malware uses the GitHub repository for downloading TOR proxies."
CERT-UA, in its notification, says that the Jester Stealer malware "also use[s] anti-analysis techniques like anti-VM/debug/sandbox." Cyble, in its blog, confirms this, adding that the malware has several built-in checks that terminate it if it is executing in a virtualization environment.
The malware, according to Cyble's analysis, terminates itself for the following reasons:
- First, the malware compares the string "-debug" with the command line parameter of the running sample. If it matches, the malware identifies that it is being debugged and terminates its execution.
- The malware checks the presence of virtualization applications, such as Virtulbox, vmbox, VMware, etc., and terminates its execution if they are identified to be running actively in the system.
- The malware specifically checks for a sandbox dll
"SbieDll.dll"and terminates its execution if it is present in the targeted machine. - The malware uses an anti-repeat technique to make sure it executes only once on any given machine. Upon execution, the malware creates a registry key value "state" and sets the value to 1. If the malware executes again on the same machine, it checks the state from the registry and terminates if the value is already set.
Once all the checks are passed, the malware creates text files titled AutoFill, Cookies, Tokens, Account, Credman, Passwords, Wallets, Networks, Autofill, Vault, Servers, Bookmarks and CreditCards to save the stolen data, Cyble says. "The malware stores all the stolen data in the memory during execution and zips it for exfiltration purposes," it adds.
To exfiltrate the stolen data, the TOR proxy is downloaded from the GitHub repository and is configured over port 9050, which is generally used for TCP/UDP communication. It then sends the data to a server hosted on the TOR, Cyble says. The malware also has a backup mechanism in place if the data is unable to get to the TOR server. "It tries uploading it (the zip file) to AnonFiles, a public yet anonymous file hosting server where the zip file name appears in the following format: "AttackerName_username_systemname.zip," Cyble says.
Cyble and CERT-UA both say that the Jester Stealer malware is not used as a persistent attack vector. Post-exfiltration, the malware deletes itself, making it difficult for detection mechanisms to track it.
Jester Stealer-as-a-Service
According to Cyble, the malware has been advertised on several underground forums since July 2021. This date corresponds to the creation date of July 20, 2021, for the "Official [Telegram] Channel" of this malware-as-a-service called "Jester Premium Channel." Information Security Media Group verified the posts and details on the channel and found that its owners have placed advertisements for the malware features and functions and even pricing details on their channel since that date.
The Jester Stealer malware owners say it has the following features:
- The connection is encrypted using the AES-CBC-256 algorithm.
- Servers can be located on the TOR network.
- All logs will be redirected to your Telegram bot.
- There is protection against running on virtual machines and sandboxes, and the malware has anti-repeat startup and self-removal.
- There is very fast collection of logs in memory without writing any data to disk.
The malware owners offer staggered pricing, based on time and services required:

The Jester Stealer Telegram posts seen by ISMG show that the malware has frequently received updates, and the version 7 builder is currently on sale.
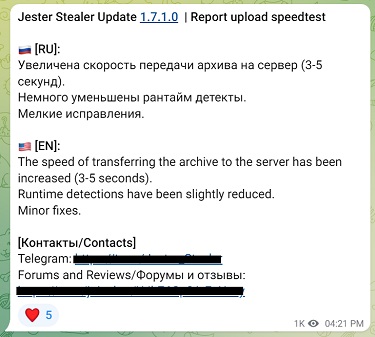
With every update, Cyble says, the malware's capability and features appear to get better. The latest version of the builder was last updated on Jan. 21, 2022, according to the Telegram post.
Other Stealer Campaigns
CERT-UA has also issued a separate alert for malicious activity from the APT 28 aka Strontium threat group, which it says is targeting Ukrainians with CredoMap_v2 malware.
The phishing email used in this campaign appears to come from CERT-UA and contains a malicious attachment that appears to be a password-protected RAR archive "UkrScanner.rar," the CERT-UA says.
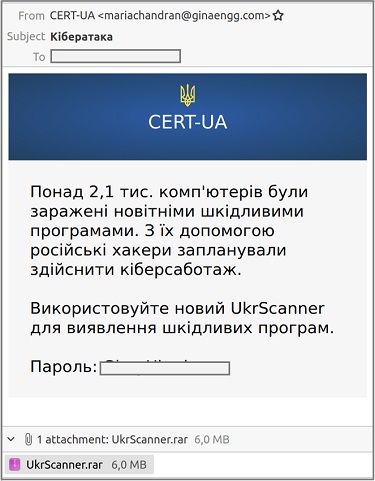
But unlike prior versions of this stealer malware, the latest one "uses the HTTP protocol for data exfiltration," CERT-UA says, adding that "stolen authentication data is sent to a web resource deployed on the Pipedream platform through the HTTP POST requests."