Encryption & Key Management , Next-Generation Technologies & Secure Development , Security Operations
Linux KillDisk Ransomware Can't Decrypt
Are Attackers Running a Ransomware Campaign or a Psychological Operation?
Disk-wiping malware known as KillDisk, which has previously been used in hack attacks tied to espionage operations, has been given an update. Now, the malware works on Linux as well as Windows systems and also includes the ability to encrypt files, demand a bitcoin ransom and leave Linux systems unbootable.
See Also: Take Inventory of Your Medical Device Security Risks
Multiple security firms have been tracking the use of the KillDisk wiper malware, particularly against targets in Ukraine.
That includes an ongoing series of online attacks against multiple financial institutions that began on Dec. 6, 2016, according to security researchers at Slovakia-based IT security firm ESET. Since those attacks began, versions of KillDisk have emerged that can infect not only Windows, but also Linux workstations - and potentially Linux servers - with a ransomware variant, ESET says. But the Linux variant appears to create an encryption key that never gets saved to disk or relayed to attackers, meaning that even if victims pay the ransom demand, there's no way they would ever receive a decryption key.
The emergence of the Windows crypto-locking KillDisk variant was first spotted by Framingham, Mass.-based security firm CyberX. The firm says it believes that the malware is tied to the Telebots group, which appears to have evolved from the Sandworm - aka BlackEnergy - gang. "We believe the malware is being distributed via malicious Office attachments," the firm says in a Dec. 27, 2016, blog post. It notes that some versions of the malware display a screen with imagery pulled from the "Mr. Robot" television show.
Crypto-Locked Linux Won't Boot
ESET, meanwhile, first spotted the Linux variant of the updated KillDisk malware. It says the Linux version overwrites the GRUB bootloader - the first code to run when a Linux system gets booted - to prevent it from booting, instead displaying only a ransom message. The Windows variant, meanwhile, encrypts files using a 256-bit AES encryption key, then encrypts the symmetric AES key - required to decrypt the data - using a 1024 bit RSA key.
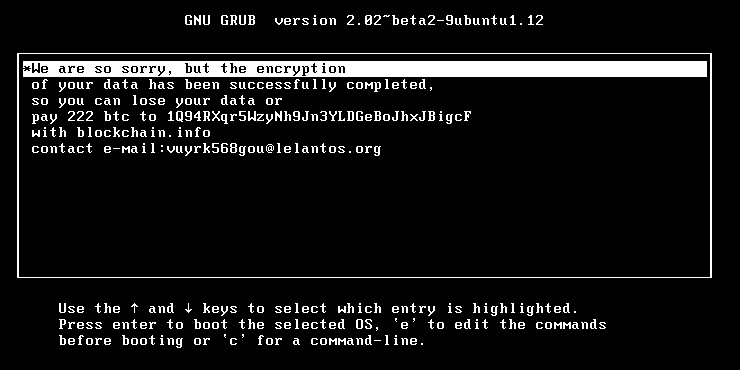
Security experts say that the ransom messages display the exact same content: the ransom amount, bitcoin address for paying the ransom as well as a contact email for the attacker registered with lelantos.org, a secure, anonymous email service. A message sent to the listed email address wasn't immediately returned.
The ransom demand is the same for both Linux and Windows systems: 222 bitcoins, currently worth about $210,000.
Not paying the ransom, however, is a good move.
For starters, as law enforcement agencies and cybercrime experts have long advised, victims should ideally never pay ransoms because they fund continuing cybercrime operations and are no guarantee that attackers will actually decrypt files.
In the case of KillDisk, however, it's not even clear if attackers would be able to provide a decryption key - at least for the Linux version. "It is important to note that paying the ransom demanded for the recovery of encrypted files is a waste of time and money. The encryption keys generated on the affected host are neither saved locally nor sent to a C&C server," ESET security researchers Robert Lipovsky and Peter Kálnai say in a blog post. "Let us emphasize that - the cyber criminals behind this [Linux] KillDisk variant cannot supply their victims with the decryption keys to recover their files, despite those victims paying the extremely large sum demanded by this ransomware."
Psychological Warfare?
The evolution of KillDisk from disk-wiping malware to also functioning as crypto-locking ransomware appears to be a cynical, psychological ploy by attackers. Instead of simply wiping systems, as KillDisk has previously done, attackers can encrypt them - still effectively putting the data beyond reach - while taunting victims with the possibility of getting their data restored if they send attackers a massive payoff.
To date, however, no one appears to have paid the ransom, at least based on the blockchain record for the bitcoin address published in ESET's report. So far, the account has only recorded one transaction, of 0.0001 bitcoins - worth just $0.10 - which was likely attackers testing the account before listing it in their ransomware.
One upside for Linux - but not Windows - victims of KillDisk, ESET adds, is that attackers appear to have slightly fumbled their crypto, "which makes recovery possible, albeit difficult." But don't count on future versions to have the same flaw.
Linux Ransomware: Unexpected Move
The move to target Linux systems with crypto-locking ransomware is an unusual evolution on two fronts, the ESET security researchers say. First, attackers seeking to maximize the bang for their buck don't typically target Linux servers.
Second, whereas ransomware is a hallmark of cybercrime gangs, KillDisk has previously been tied to apparent cyber-espionage operations, including November 2015 attacks against Ukrainian news agencies. After parts of Ukraine's power grid experienced blackouts in December 2015, furthermore, investigators also reported that both the BlackEnergy 3 cyber-espionage Trojan and KillDisk disk-wiping malware were recovered from at least one of the affected power provider's Windows PCs, meaning that attackers have also been targeting industrial control and SCADA systems.
It's not clear if attacks against Ukrainian energy providers have been continuing. Last month, Ukraine's national power company, Ukrenergo, reported that it was investigating whether Dec. 17, 2016, blackouts were the result of a hack attack (see Ukrainian Power Grid Blackout Alert: Potential Hack Attack). Ukrenergo has yet to comment further on the results of its investigation, however, so the blackout might not have been the result of a hack attack.
Separately, several security firms have noted that the Sandworm - aka BlackEnergy - group may have morphed into
But it's not clear if KillDisk is used solely by one group of attackers, or what their motives might be. As the ESET researchers note: "Any ties between orchestrators of these attacks remain unclear and purely circumstantial."



















