Blockchain & Cryptocurrency , Cybercrime , Endpoint Security
Hacked MicroTik Routers Serve Cryptocurrency-Mining Malware
Researchers: Attackers Have Compromised More Than 209,000 Routers
More than 209,000 carrier-grade routers made by the Latvian company MicroTik have been infected with two types of software that mine cryptocurrency, security researchers say.
See Also: An Assume-Breach Mindset: 4 Steps to Protect What Attackers are After
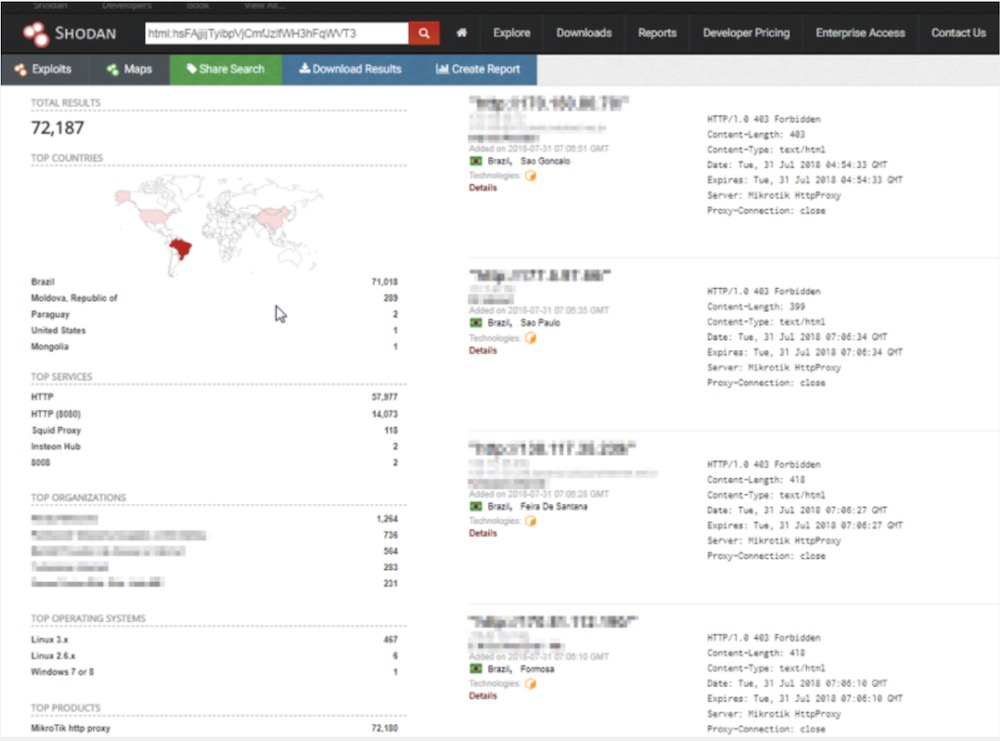
Most the devices are in Brazil, Troy Mursch of Bad Packets Report says via Twitter.
I've notified @certbr as the majority of the devices found are in Brazil. https://t.co/2WMZsspSvo
— Bad Packets Report (@bad_packets) August 3, 2018
Security researchers report that the devices have been seeded with either Coinhive or Crypto-Loot, which are small JavaScript programs that mine for monero, a privacy-focused cryptocurrency.
The MicroTik devices that have been targeted are routers that are used by ISPs and businesses that serve up to hundreds of users per day, writes Simon Kenin, a security researcher with Trustwave's SpiderLabs, who posted an in-depth analysis of the campaign.
"Let me emphasize how bad this attack is," Kenin says. "The attacker wisely thought that instead of infecting small sites with few visitors, or finding sophisticated ways to run malware on end user computers, they would go straight to the source: carrier-grade router devices."
Monero Mining
Mining is the process by which transactions are confirmed on a blockchain. Miners use computers to churn out random hashes in hopes of completing a block and receiving an award. In its early days, bitcoin could be mined on consumer hardware, but now it's mostly mined using specialized ASIC - for application-specific integrated circuit - rigs.
But many cryptocurrencies, including monero, can still be mined using consumer-grade hardware.
"The attacker wisely thought that instead of infecting small sites with few visitors, or finding sophisticated ways to run malware on end user computers, they would go straight to the source: carrier-grade router devices."
—Simon Kenin, Trustwave
Cryptomining attacks occur when the JavaScript mining code is planted on a web page and begins running in the background without the knowledge of the user. Of all cyberattacks, it is among one of the most benign, but it still consumes processing power and extra electricity.
Many security products now automatically block cryptomining software from running because it's frequently deployed either secretly or without full disclosure to web surfers (see Cryptojacking: Mitigating the Impact).
The prevalence of cryptomining attacks often rises and falls in accordance with the price of monero. According to Coinmarketcap, one monero coin was trading at around $116 on Friday - a relatively low value not seen since November 2017.
But attackers have shown growing interest in cryptomining because the schemes can require less effort than running ransomware campaigns. Indeed, attackers can target known flaws to automatically install mining malware in a large number of devices, meaning they don't have to interact with end users - victims - to try and shake them down for a ransom to unlock their data (see Cryptojacking Displaces Ransomware as Top Malware Threat).
Unpatched Devices
In the case of the MikroTik router-targeting campaign, attackers appear to have used an exploit for a vulnerability that MicroTik patched on April 23, Kenin says. The attack targets Winbox - an administrator utility for MicroTik's RouterOS.
"To MicroTik's credit, they patched the vulnerability within a day of its discovery, but unfortunately there are hundreds of thousands of unpatched - and thus vulnerable - devices still out there, and tens of thousands of them are in Brazil alone," Kenin says.
The attackers figured out how to inject the Coinhive script into every web page that a user visits, Kenin writes. He found that if a user encounters an error on a web page, the Coinhive script would be launched. But it may be possible that the script is injected into every web page that is browsed by someone whose connectivity comes from an infected router.
"How this is done exactly, we don't know yet," Kenin writes. "However, the attacker is clearly showing a high level of understanding of how these Mikrotik routers work."
The cryptomining attack also appears to be able to work against systems that access a router. For example, if an Apache server that is hosting a website is on the same router, the pages it serves are also affected.
"In other words, the attack works in both directions," Kenin writes.
Developing Attack
It appears the attackers remain hard at work. Kenin writes that the script that the attackers are using to infect vulnerable routers was updated "a few times" even as he was writing his blog post on Friday.
Using Censys.io, Mursch found other vulnerable hosts. He identified at least two other campaigns that have been targeting MicroTik devices, based on Coinhive-specific keys. Each key ensures that payments get funneled to the right entity.
As of Mursch's last count, 209,501 MicroTik devices had been compromised by attackers.





















