Blockchain & Cryptocurrency , Business Continuity Management / Disaster Recovery , Critical Infrastructure Security
Ransomware Payments: Just 46% of Victims Now Pay a Ransom
Average Ransom Payment, When a Victim Pays, Drops to $211,529, Coveware Reports
Is the tide finally turning on ransomware?
One piece of good news is that the number of organizations hit by ransomware who choose to pay a ransom to their attackers has been declining, reports ransomware incident response firm Coveware.
Based on thousands of cases on which it has worked, Coveware says the number of ransomware-hit victims who paid a ransom declined from 85% in Q1 of 2019 to 46% in Q1 of this year.
"This is what progress looks like against ransomware," Coveware says in a new report. "It is slow. There is no single variable that explains it, but it is fact."
Coveware CEO Bill Siegel tells me: "The trend is not surprising, but as you can see from the duration of the chart, it is subtle over time and not something you can draw inferences from, quarter to quarter."
Coveware's findings stand in contrast to a recently released study from Sophos, which noted that the number of organizations that self-reported paying a ransom had increased from 2020 to 2021. But that study was based on a self-reported survey, whereas Coveware's findings are based on actual cases.
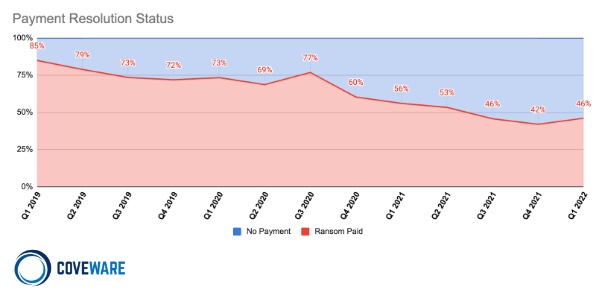
When victims do pay a ransom, in Q1 they paid an average of $211,529, down 34% from the previous quarter, Coveware found. It attributes this to fewer victims paying, attackers overall infecting smaller organizations - given the law enforcement fallout they often face after hitting very large businesses - as well as the erosion of established ransomware-as-a-service brands.
What should organizations be doing to better blunt attacks? In terms of initial attack vectors tied to successful attacks, Coveware found that while phishing attacks and compromising remote desktop protocol connections continue to dominate, followed by attackers exploiting software vulnerabilities, the incidence of social engineering attacks has been noticeably increasing. To combat this, it recommends both user training - especially for IT help desks - as well as blocking the installation of legitimate but unapproved remote access tools on systems "such as TeamViewer, LogMeIn or GoToAssist."
Market Share: Conti and LockBit Dominate
In the first quarter of this year, Coveware found that these ransomware strains had the most market share:
- Conti v2: 16.1%
- LockBit 2.0: 14.9%
- BlackCat - aka Alphv: 7.1%
- Hive: 5.4%
- AvosLocker: 4.8%
Ransomware-as-a-service operations typically involve operators who develop and supply their crypto-locking malware and affiliates - aka business partners - who take the malware and use it to infect victims. For every victim who pays, an affiliate will often receive 70% of the payment, while the rest goes to the operators.
While that has been the traditional approach, security researchers say Conti has run most of its attacks in-house, backed by robust teams and subgroups focused on targeting different types of victims, as well as ongoing research and development (see: Leaks Fail to Dent Conti's Successful Ransomware Operation).
Regardless of approach, both Conti and LockBit have a relatively small market share compared to the likes of Maze or REvil - aka Sodinokibi - in years past.
One explanation for this is that after DarkSide's disastrous attack on Colonial Pipeline in May 2021 and after REvil hit meat-processing giant JBS and managed service provider software developer Kaseya - among other major attacks - affiliates care less about working with big brand names, given their reputation for getting targeted and disrupted by law enforcement agencies.
"As large RaaS brand affiliation becomes less of an asset to ransomware affiliates - due to the focus of law enforcement - ransomware affiliates are becoming very fluid in their movement and sampling of different RaaS kits, or even developing their own kits based on leaked ransomware source code, such as Hello Kitty's source code or even Conti's leaked source code," Coveware says.
In addition, it says, many attackers continue searching for a sweet spot in the size of victim they target: not so small that only a paltry ransom amount can be demanded and not so large that it leads to close attention from law enforcement agencies.
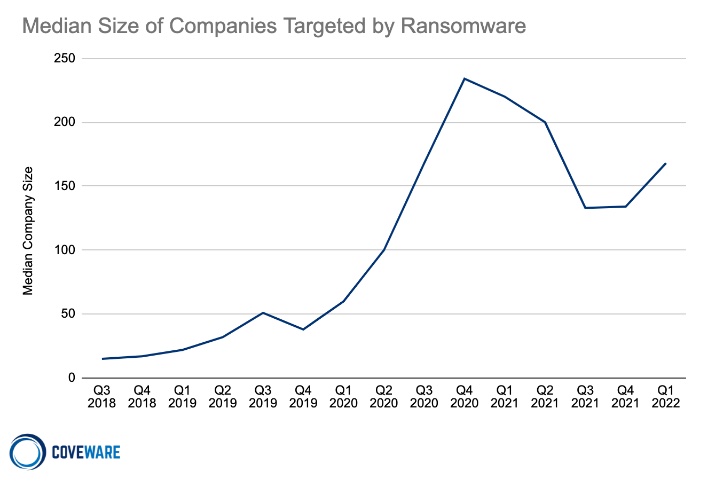
Coveware says another trend is the shift from big game hunting, involving crypto-locking large targets, to "big shame hunting," in which attackers do not encrypt data but instead steal and threaten to release it. By doing so, they can still extort victims, but perhaps without triggering a law enforcement response (see: Ransomware Attackers Eying 'Pure Data Leakage Model').
Paying for Deletion: 'Poor Decision'
As that highlights, ransomware-wielding attackers have continued to test new ways to pressure victims into paying. Such innovations have included using double extortion: stealing data before leaking systems and then threatening to name and shame victims and leaking their data. Some groups use distributed denial-of-service attacks against victims who don't quickly pay. Others contract with outsourced call centers to call victims demanding a payment - or sometimes to call their customers to try and publicly shame them into doing so.
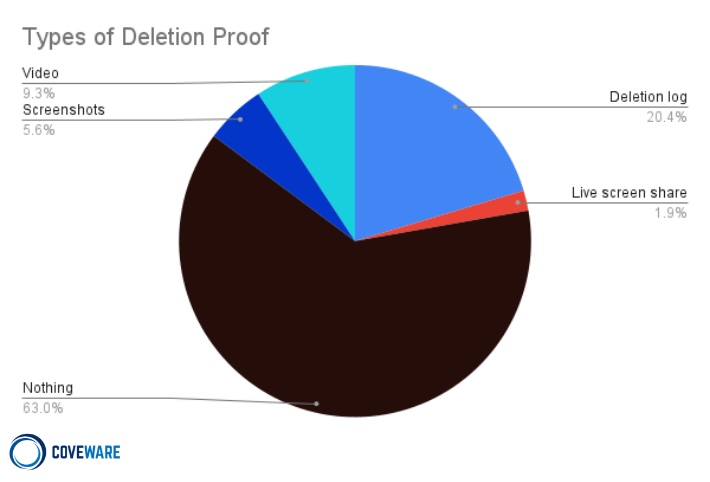
Criminals may also demand different types of payments. For example, some demand separate ransoms for a decryptor versus a promise from the crooks to delete stolen data.
Where the latter extortion attempt is concerned, Coveware's advice is simple: Don't bother. "In the majority of cases, the victims that pay to have a leak suppressed receive no evidence that their stolen data will be deleted or that they will not be extorted again in the future," it says. "In one notable case, we observed a threat actor explicitly state that they would not be deleting the stolen data if paid, and would keep it for future leverage against the victim."
Message: Stay the Course
Despite the reported reduction in the number of organizations that pay a ransom and a reduction in the average amount being paid, don't expect a quick or easy resolution to the ransomware problem; extortionists remain expert at finding innovative new ways to shake down victims. But Coveware says that if those trends do continue, the ransomware problem may appear much more diminished, say by 2025.
"In an industry where it can sometimes feel quite futile, our message to incident response first responders, defenders, and law enforcement agents is: Persistence will pay off for the good guys in the long term," Coveware says.











