Anti-Phishing, DMARC , Cybercrime , Cybercrime as-a-service
Ransomware Danger: Russian-Speaking Gang Targets Russians
Cybercrime Reminder: Russians Who Target Other Russians Play With Fire
Russian criminals operating online who want to stay out of jail need only to follow a few simple rules, the primary one being: Never target Russians.
So it's surprising that security researchers have uncovered a new ransomware-wielding gang of Russian speakers that includes Russian victims on its hit list.
Group-IB, a cybersecurity firm based in Singapore, says the gang, which it has dubbed OldGremlin, appears, since the spring, to have been launching "multistage attacks on large corporate networks of medical labs, banks, manufacturers, and software developers in Russia," using a custom set of tools to forcibly encrypt files on infected systems, after which it issues a ransom demand in return for the promise of a decryption tool.
At least one of the group's attacks, which occurred in August, has been successful, the cybersecurity firm says. In that incident, the gang targeted a Russian clinical diagnostics laboratory with spear-phishing emails carrying "Invoice" in their subject line and requesting the recipient click a link to pay an overdue bill. "By clicking the link, the victim downloaded a Zip archive that contained a unique custom backdoor, dubbed TinyNode. The backdoor downloads and installs additional malware on the infected machine," Group-IB says.

In this incident, the diagnostics laboratory was hit with a ransom demand for $50,000 worth of cryptocurrency, Group-IB says. Citing a nondisclosure agreement, it declined to say if the firm paid the ransom.
Custom-Built 'Tiny' Tools
Many ransomware-wielding attackers now tap ransomware-as-a-service offerings, with Sodinokibi - aka REvil - being the most popular. By procuring crypto-locking code as a service, attackers can focus on infecting endpoints, rather than having to keep their code base updated, ensuring that the encryption works correctly and regularly repacking the code to help evade security defenses. In return, these affiliates typically share 30% of all victims' ransom payments with the RaaS operators.
OldGremlin, however, appears to be using its own, custom-built tools and is "managing all attack stages themselves without resorting to third-party services," says Rustam Mirkasymov, head of Group-IB's cyberthreat research department.
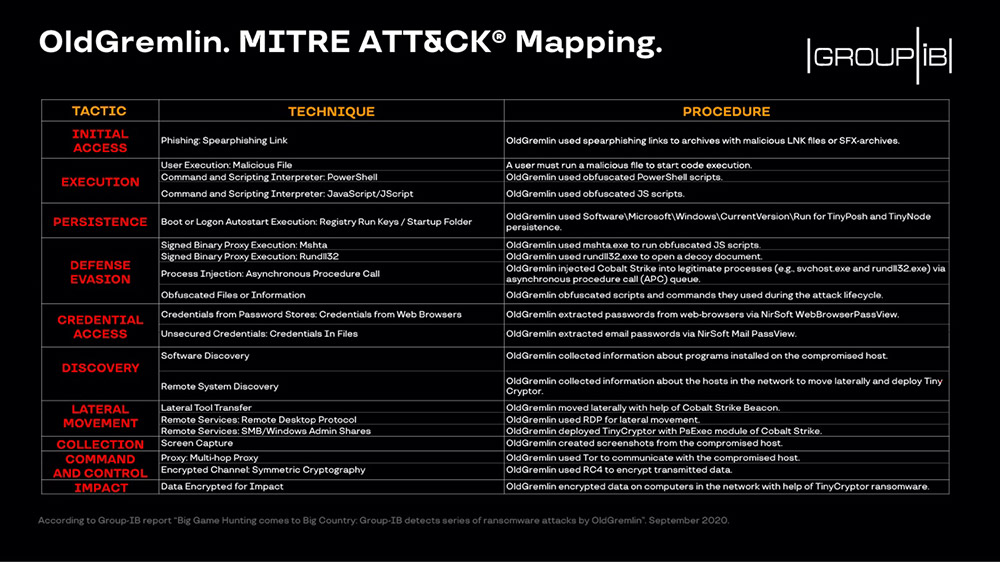
Tools tied to the group's attacks are codenamed TinyPosh, TinyNode and TinyCryptor, based on how they function.
"The PowerShell script has a command 'stArT-TINy' and a variable 'tiny-endpoint.' Thus we assumed that its developer named the Trojan 'Tiny.' But this name was already reserved by the infamous Zeus Trojan. That's why we dubbed it TinyPosh to highlight that it was written in PowerShell," Mirkasymov tells me. "Other names have been chosen to show the links with TinyPosh and for convenience, as all these tools are related to a single threat actor called OldGremlin."
The group uses TinyCryptor - aka decr1pt - to forcibly encrypt victims' systems. "TinyCryptor is written in C#," Mirkasymov says. "It's very simple, though they managed to successfully encrypt a big organization and evade detection."
Russia Neighbors?
Given the risks faced by criminals operating online, from Russia, who target Russians, Group-IB says this group of Russian speakers may instead be based in a neighboring Russian-speaking country.
"The attackers are either fine-tuning their techniques, benefiting from a home advantage before going global - as it was the case with Silence and Cobalt - or they are representatives of some of Russia's neighbors who have a strong command of Russian," says Oleg Skulkin, a digital forensics analyst at Group-IB.

Still, it's unusual for criminals in countries neighboring Russia to target Russians. Many types of malware, including ransomware, tied to Russian-speaking gangs or developers include checks to ensure that the malicious code won't execute if a system's language is set to Russian or if the system appears to be located in any of the countries comprising the Commonwealth of Independent States - including Belarus, Georgia, Russia, Ukraine and others - that was founded in 1991 after the Soviet Union dissolved.
Criminals who fail to follow these rules can see themselves serving a Russian prison sentence. One of the most famous is Dmitry E. Fedotov, aka "Paunch," who was arrested in 2013 by police in Russia. He was charged with developing the automated Blackhole Exploit Kit - a now-defunct crimeware-as-a-service offering, available on a subscription-only basis for $500 per month - plus the Cool Exploit Kit as well as the malware obfuscation service Crypt.am. Perhaps most important, however, the Blackhole gang was also accused of stealing more than $2 million from Russian banks.
3 Rules for Avoiding Russian Prison
The message was clear: Don't mess with Mother Russia. Remaining a successful Russian cybercriminal, in fact, requires following three rules:
- Rule No. 1: Never hack Russians or anyone else in a CIS nation.
- Rule No. 2: If a Russian intelligence service asks for your help, provide it.
- Rule No. 3: Watch where you vacation - especially avoiding countries that are friendly with the U.S. That's because those travels could lead to extradition to face charges.
Apparent Exceptions: Cobalt and Silence
Of course, as Skulkin notes, there are at least two notable exceptions to the above, including:
- Silence: This gang, which first came to security researchers' attention in 2016, was known for running ATM jackpotting - aka "cashout" attacks - inside Russia and other CIS nations before moving its focus to other countries and refining its tactics. Last year, Group-IB said a $3 billion bank heist in Bangladesh appeared to have been the work of Silence.
- Cobalt: This gang was also tied to attacks against banks - graduating from jackpotting Russian ATMs to hacking foreign payment gateways, card processing systems and issuing fraudulent SWIFT money-moving messages - since at least 2016, racking up more than $1 billion. The group has continued to operate even after Spanish police arrested "Denis K.," a Ukrainian they accused of laundering bitcoins worth millions of dollars for the gang.
Silence and Cobalt seem to have successfully escaped the startup period in which they targeted other Russians. But that doesn't mean they escaped notice by authorities. Indeed, there are well-documented ties between Russian criminal enterprises and the country's intelligence services and nation-state attack groups.
Hence the gangs may not just have graduated from attacking Russians to only hitting non-allied countries - they may also be doing favors for spy agencies.
So goes the Russian cybercrime success story.











