Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Ransomware
Canceled: Crowdfunding to Pay Shadow Brokers for Exploits
Legal Concerns Cited as Researchers Shutter Effort; Debates Still Rage
Two researchers who launched a crowdsourced effort to subscribe to a monthly service designed to leak stolen exploits - while simultaneously querying the information security community about whether it was a good idea - have dropped their effort, citing legal concerns (see Ethical Debate: OK to Pay Shadow Brokers for Exploit Dumps?).
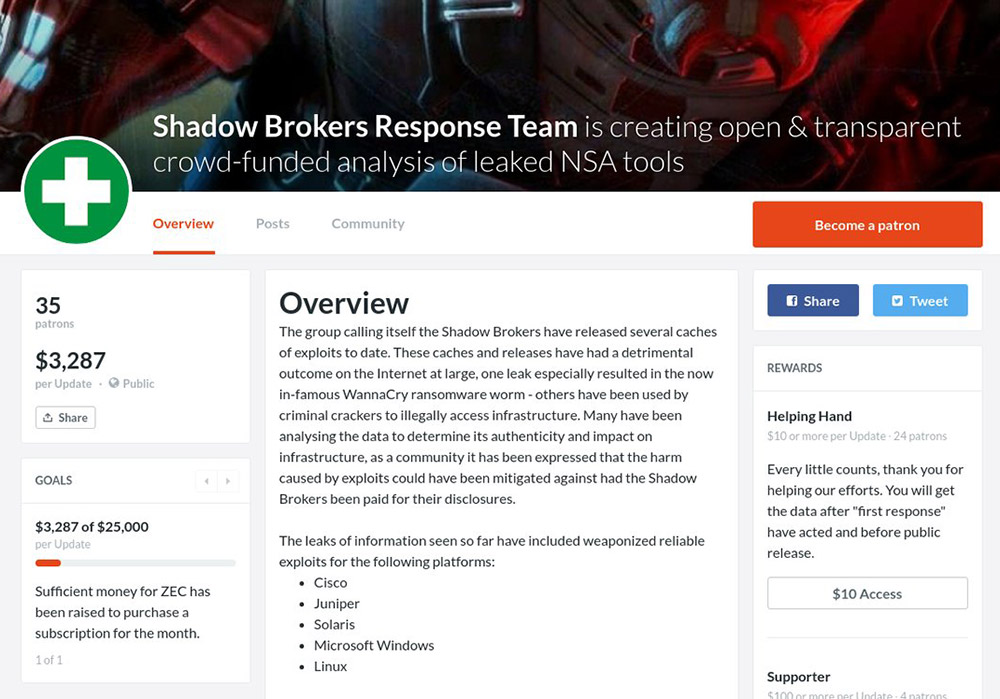
Forty-eight hours after launching a crowdsourcing effort on Patreon, seeking to gather $25,000 per month, Manchester, England-based security researcher Matthew Hickey, aka Hacker Fantastic, and the French security researcher know as x0rz, announced Thursday that they've suspended their campaign.
The money was to be used to pay the subscription fee for monthly dumps of attack tools by the Shadow Brokers. That group - its identity remains unknown - promised to provide a first look at attack tools, stolen from the "Equation Group," that it planned to leak, to anyone who ponied up the subscription fee. Whether Shadow Brokers would have honored that promise, however, remains uncertain (see Shadow Brokers Promises Exploit of the Month Club).
The two security researchers were clear that even if the subscription got paid, the effort might fail. But they said the effort could be worth it if it gave the information security community a heads-up on forthcoming exploits. For example, the Equation Group's EternalBlue attack tool, which was dumped in April, got used by attackers to create a worm that targeted Windows systems with an unpatched server message block flaw, to install WannaCry ransomware.
The researchers also solicited the information security community's feedback on what they were doing, via a Twitter poll.
Is a KickStarter project to pay Shadow Brokers subscription ($20k) and then perform analysis on it and responsible disclosure a good idea?
— Hacker Fantastic (@hackerfantastic) May 30, 2017
But they have since called off their effort.
"Due to legal reasons I'm now retracting from the crowdfunding started to acquire the #ShadowBrokers dump," x0rz says in a Thursday statement posted to Pastebin. "It was very interesting talking with all regarding this crowdfunding. As it is new territory we should be very cautious, hence my retraction from this project."
Crowd-Funded Cyber Arms Acquisition Attempt
Hickey, in a statement issued Thursday via Twitter, also cited legal concerns. "If you ever want to hear a lawyer shout expletives at volume down a phone you need to call him and tell him that you have created the first open source crowd-funded cyber arms acquisition attempt," he says. "It transpires that should funds change hands from ours to the Shadow Brokers we would be certainly risking some form of legal complications. It was just too risky and the advice was under no circumstances to proceed further with this."
No intelligence agency or government has attributed the identity of the Shadow Brokers.
But the researchers say they received a heads-up from law enforcement officials that the group has strong links to the Russian Federal Security Service, known as the FSB, which was previously known as the KGB. As a result, the researchers were warned that they might "fall afoul of the U.S. justice system."
Hickey had told me that if the NSA chose to release details of the tools that Shadow Brokers now possesses, then they would call the crowdsourcing effort off.
Refunds Coming
At the time of the project's cancellation, $3,287 had been pledged by 35 backers, all of whom received a cat video as thanks.
The researchers have promised to refund all donations. That includes 0.25 bitcoins, worth about $630, which X0rz says will be returned to their owners, provided donors "can cryptographically prove the transaction is yours" via an email to him. Any remaining funds, he promises, will be donated to the Electronic Frontier Foundation.
Ethical Debate
The researchers' move to crowdsource funding to pay the monthly Shadow Brokers subscription fee, and to then share that information with other information security researchers, has triggered extensive debate. Some argued strongly for or against, while others seemed ambivalent.
"Raise dosh for cyber crooks who stole from guv crooks to stop the other cyber crooks from committing cyber crookery," read one tweet - since deleted - responding to my initial report.
Other information security professionals said they supported the effort, arguing that it would make the world a safer place.
I feel this will create more dumps due to the finiancial gain, but the more dumps we buy the safer systems will be overall. so do it IMO.
— Scott Grange (@Caldaeon) May 31, 2017
Some, however, argued against it, not least because it would be paying criminals.
Never... why put money in their pockets? We don't know the connections these people have - terrorist cells, drug rings, human trafficking
— A Girl Has No Name (@4GirlHasNoName) May 31, 2017
Some information security experts that I queried about the proposal told me they were ambivalent. Most denounced it.
"I personally would have zero to do with this," Sean Sullivan, a security adviser at Helsinki-based security firm F-Secure, tells me.
Many also warned that paying could create a dangerous precedent. "To pay Shadow Brokers would encourage further such thefts, and so I'm afraid as much as I'd like to see what they have to say, I think it a poor idea," says Alan Woodward, a computer science professor at the University of Surrey and a cybersecurity adviser to the EU's law enforcement intelligence agency, Europol.
Failed Premise?
The operational security expert known as the Grugq argues that the goal of the endeavor - to give the good guys copies of the exploits earlier so they can help organizations patch their systems - doesn't work. For example, he noted that Microsoft in March issued a fix for the SMB flaw for all supported operating systems. After Shadow Brokers leaked the EternalBlue exploit tool in April and WannaCry attackers began targeting the SMB flaw May 12, however, it turned out that many organizations had yet to apply Microsoft's patch.
"Getting white hats NSA exploits will save the internet" is a provably false theory. It didn't work last time.
— the grugq (@thegrugq) June 1, 2017
One Way Forward: Private Notifications
In January, Shadow Brokers named Equation Group tools - including EternalBlue - that they planned to dump. That appears to have led the NSA to tip off Microsoft about the SMB flaw. In February, Microsoft canceled its monthly release of patches - a very unusual move. In March, it quietly released updated versions of its supported operating systems that had patches for the SMB flaw. In April, Shadow Brokers leaked the attack tool.
Woodward recommends this back-channel model for fixing flaws over any crowdfunded efforts to pay exploit leakers with unclear motivations and allegiances. "If there is a government agency who knows that a further breach may contain exploits that could be damaging if let out in to the wild - just like EternalBlue - then they can liaise directly with the vendor concerned to get it sorted soonest," he tells me.











