Access Management , Cybercrime , Endpoint Security
10 Initial Access Broker Trends: Cybercrime Service Evolves
$5,400 Is the Average Price for Access to Hacked Networks, Kela Reports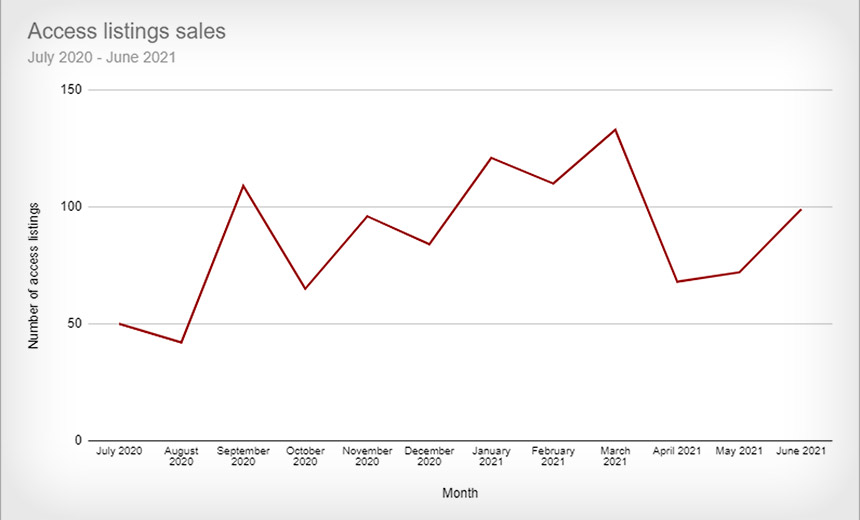
The rise of ransomware as a moneymaking powerhouse for online attackers parallels the services being offered by initial access brokers. Such brokers sell access as a service to others, saving them the time, effort and expense of gaining a toehold in an organization's network.
See Also: Cybersecurity for the SMB: Steps to Improve Defenses on a Smaller Scale
Initial access brokers gain first access to victims' networks in a variety of ways - often via weak remote desktop protocol or remote management software to which they've gained brute force access. Sometimes, attackers exploit an unpatched vulnerability in a system. Whatever the approach, once they have access, brokers can resell it to others, sometimes more than once (see: Ransomware's Helper: Initial Access Brokers Flourish).
For criminals, the advantage of buying ready access to a corporate network is easy to see: Instead of spending time trying to identify victims and gain remote access, buyers can select from a menu of options, picking victims based on their revenue, country and sector, as well as the type of remote access being offered.
As cybersecurity firm CrowdStrike has noted: "When criminal malware operators purchase access, it eliminates the need to spend time identifying targets and gaining access, allowing for increased and quicker deployments as well as higher potential for monetization."
For ransomware-wielding criminals in particular, buying access can cost a fraction of what a successful ransom payment brings in, without the hassle of trying to hack into a victim's network first. Security experts say crime gangs practicing big game hunting - taking down large targets in search of bigger ransoms - are especially reliant on initial access brokers for target selection.
So goes the initial access broker business model in recent years, with demand remaining heavy from attackers who wield crypto-locking malware.
What's the current state of the initial access market? Israeli threat intelligence firm Kela reviewed 1,000 access listings offered for sale on publicly accessible cybercrime forums over the past year, of which at least 262 were allegedly confirmed to have been sold.
Based on those listings, here are 10 trends it found:
1. Affordable Access
For the period from July 1, 2020, through June 30, Kela reports that the average price for remote access to a network was $5,400, while the median price was $1,000.

For comparison's sake, the average ransom paid by a victim in the second quarter of this year was $137,000, according to ransomware response firm Coveware.
2. RDP and VPN Credentials Rule
Remote desktop protocol and VPN credentials were the most common types of access being listed. But other types of access also get offered - for example, via remote management software, which many managed service providers will install on the endpoints they manage for customers.
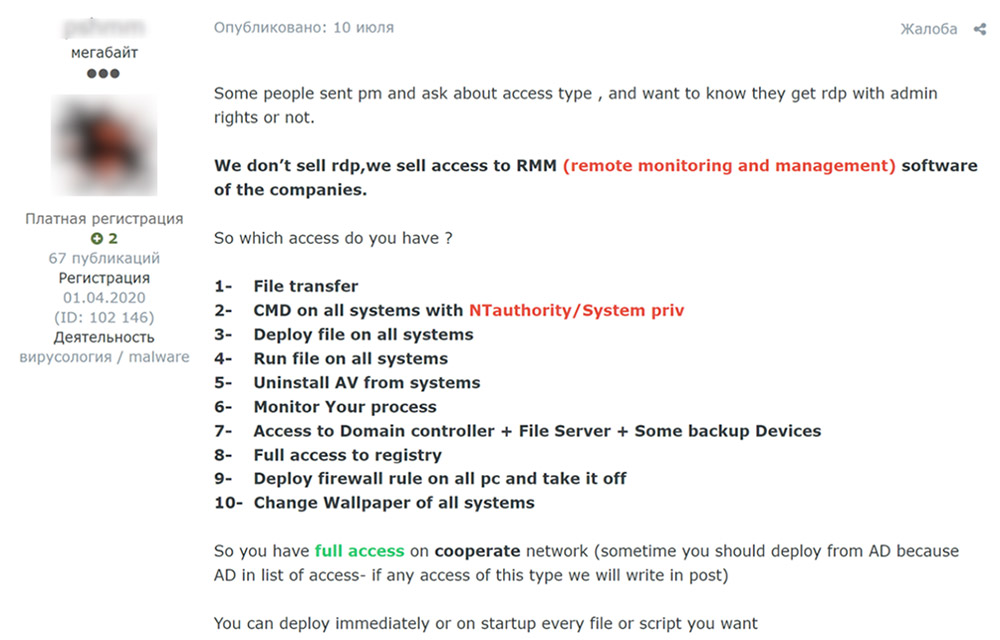
Some attackers also offer access to specific types of environments. For example, "VMWare's ESXi servers have recently become quite popular among ransomware attackers," says Victoria Kivilevich, a threat intelligence analyst at Kela who wrote the new report.
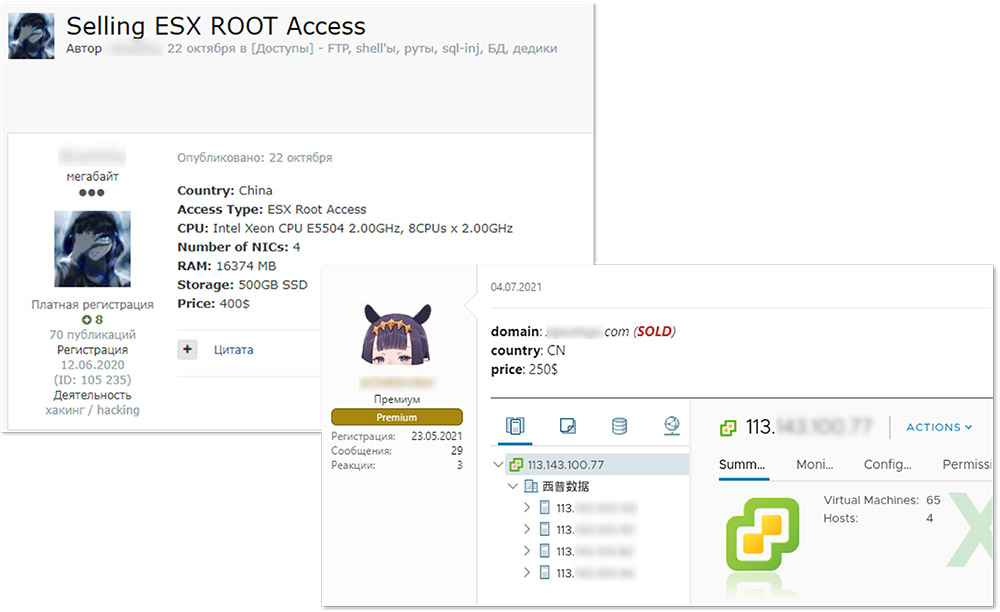
Indeed, REvil - aka Sodinokibi - as well as DarkSide and now BlackMatter have all built malware capable of crypto-locking Linux devices running ESXi servers so their data can be held for ransom.
3. Active Directory Credentials: Extra Valuable
"The most valuable offers include domain admin privileges on a computer within a company with hundreds of millions of dollars in revenue," Kivilevich writes in the report. Having domain-admin access to Microsoft Active Directory means an attacker can use the IT tool to distribute crypto-locking malware onto every endpoint inside an organization. Forcibly encrypting more systems at once might increase the chance that a victim pays a ransom in exchange for the promise of a decryption tool.
4. Top Target: US Organizations
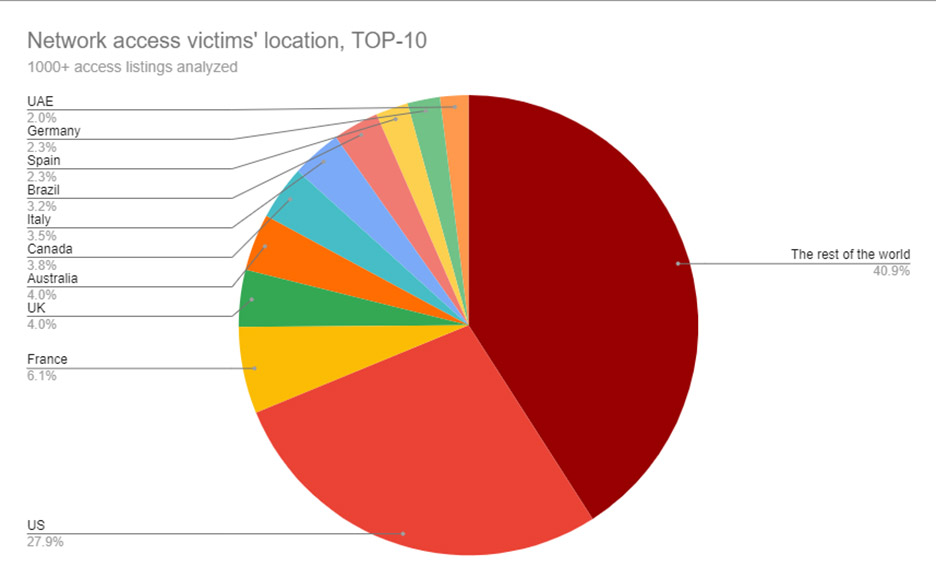
The greatest number of remote access credentials being listed, Kela found, were for targets in the United States, which accounted for 28% of all listings, followed by France, the U.K., Australia, Canada, Italy, Brazil, Spain, Germany and the United Arab Emirates.
5. Access to Manufacturing Leads Offerings
Organizations in the manufacturing sector were most listed, followed by education, IT, financial services, government and healthcare. And brokers didn't just sell access to large firms; Kela notes that there were "plenty of offers" for access to small firms, often retailing for $100 to $200.
6. One Buyer Often Preferred
Some brokers will list a sample of the access they have for sale and tell buyers to contact them for more details.
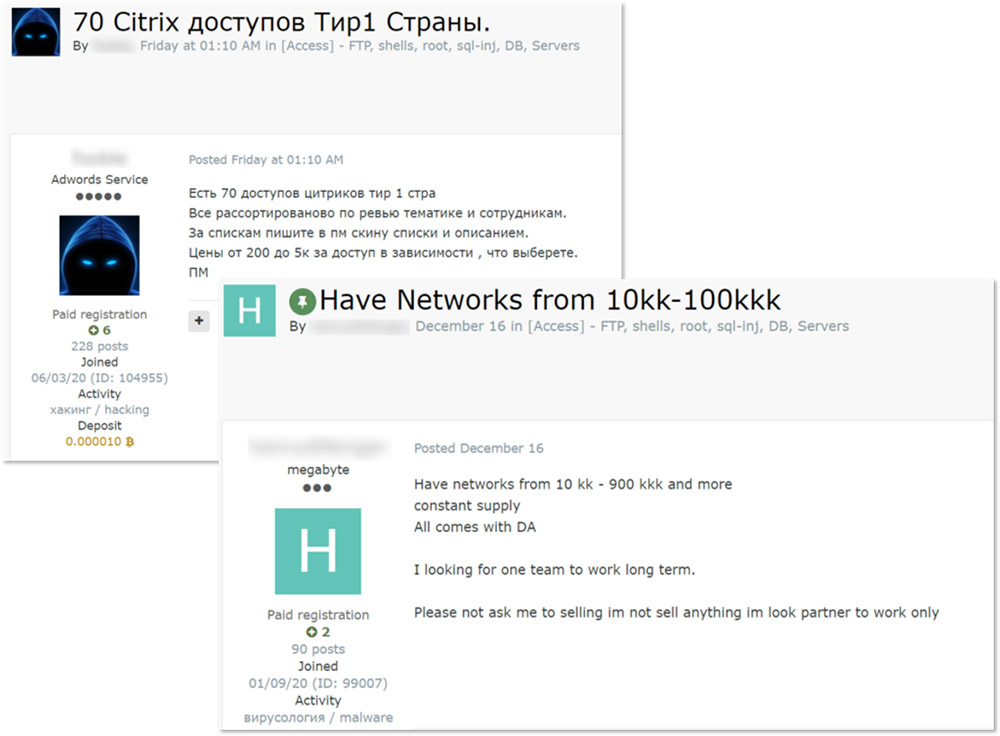
"These brokers generally are interested in getting one buyer for all the accesses being sold and sometimes go as far as to request a percentage of the ransom if an attack is successful," Kivilevich says.
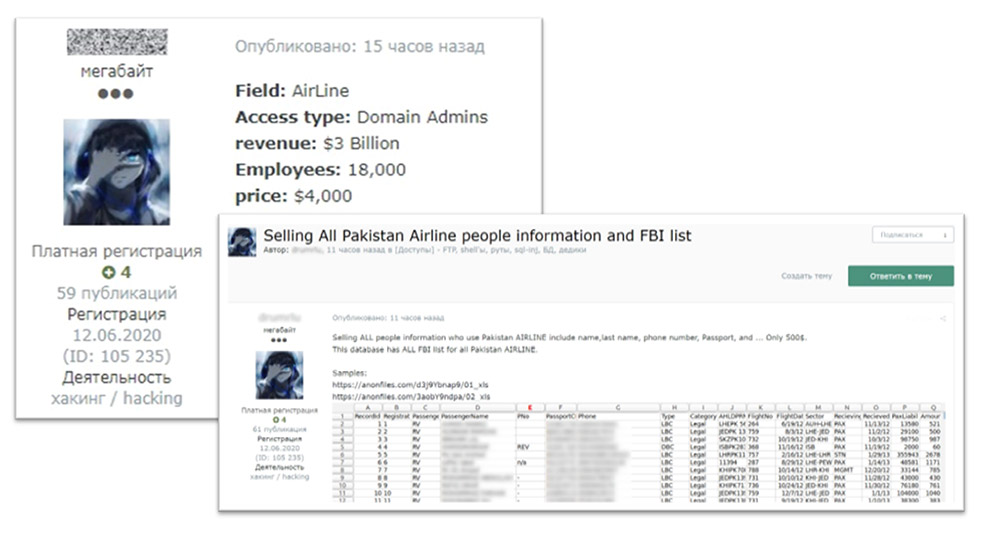
7. Multiple Monetization Strategies
Some network access brokers appear to sell not just access but also data from victims' environments. One example involved Pakistan International Airlines, to which a broker was selling access for $4,000 late last year. "A week after putting up access to the airline's network, the actor announced that he was also selling all the databases from the airline's network," according to Kela. "Therefore, the actor took two different approaches to try and monetize, leveraging the network access to the airline's network that he obtained to exfiltrate the company's data."
Numerous threat intelligence firms now monitor underground forums for details on potential victims. While this is a paid service, the intelligence gleaned by such monitoring can give victims the ability to more quickly lock down network intrusions they may have missed.
"The time between network access for sale and a ransomware attack occurring is not imminent, therefore the earlier the detection of weakness in your organization's network, the better chances your security team will have to mitigate that weakness and prevent further damage from a ransomware attack," Kivilevich writes.
8. Brokers React to White House Moves
In recent months, ransomware has become a political hot potato. The Biden administration has demanded that Moscow crack down on criminals hitting U.S. targets from inside Russia, threatening to disrupt them directly if Russian authorities don't act soon (see: Has REvil Disbanded? White House Says It Doesn't Know).
In response, some cybercrime forums - including the Russian-language Exploit and XSS forums - have announced bans on ransomware, although security experts say such prohibitions are not always heavily enforced. Likewise, some initial access brokers appear to have grown more cautious about listing some types of victims, such as healthcare entities.
9. Private Communications Still Happening
But such sales may well still be occurring behind the scenes. Last year, for example, Kela's Kivilevich reported that some brokers were "posting victims from the healthcare sector and then deleting the offers after the criticism from other users" as the pandemic continued, but likely sold them via other means later.
The initial access broker scene is never static. Security experts say new sellers appear constantly, advertising access to yet more fresh victims. But understanding how many organizations have been hit can be difficult, because not all types of access get posted on cybercrime forums. And even when they do, brokers will often obscure the victim's identity, because, of course, they wouldn't want to see the victim get tipped off.
While some forums have restricted ransomware discussions, would-be initial access broker buyers, of course, don't have to say why they're buying such access. Furthermore, while Exploit and XSS banned accounts held by administrators for groups such as DarkSide and REvil, these groups could have simply created new accounts in other names to continue purchasing access or building relationships.
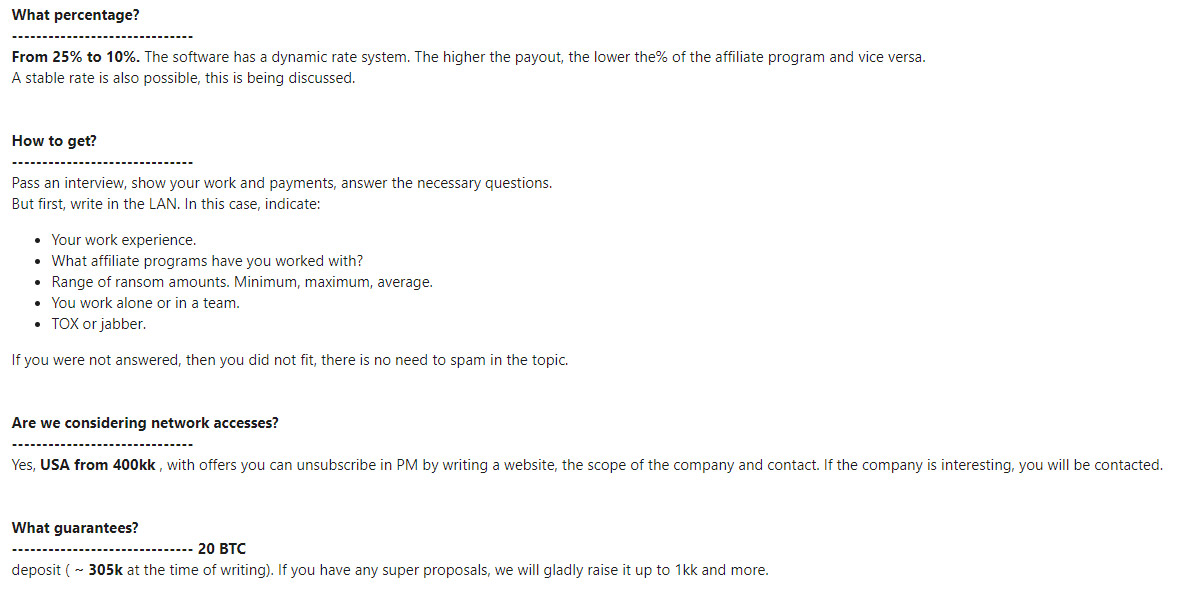
10. Dominant Groups Foster Relationships
Many established brokers appear to form relationships with specific crime groups or affiliates of ransomware operations, leading to them no longer listing their "accesses" for sale on public cybercrime forums, but rather sharing them via private conversations, Kivilevich says.
She says the number of access listings declined in Q2, compared to previous quarters, which may reflect such a shift. Multiple brokers will list partial details on a cybercrime forum, for example, and tell would-be buyers to communicate privately for more details.
Ransomware operators seeking access brokers for exclusive business relationships - or at least a right of first refusal - is a trend that appears to have begun by at least the end of last year. That's when the DarkSide ransomware-as-a-service operation posted on cybercrime forums that it wanted to find brokers who could give it access to U.S. businesses with at least $400 million in annual revenue.
Many larger ransomware operations appear to have cultivated an extensive list of connections and built well-established relationships, says Bob McArdle, director of cybercrime research at security firm Trend Micro. While the individual ransomware groups might come and go, there's nothing to stop operators and affiliates from carrying these connections with them when they leave to start or join new groups.






















